Anticipating Cybersecurity from the Design Stage
“The process of security is not a feature you validate at the end of a project.No test can patch a flaw born of poor design.”— Bruce Schneier, The Process of Security
In 2025, cyber-threats are evolving faster than ever: compromised software supply chains, known but unpatched vulnerabilities, the rise of malicious AI…
Amid this growing complexity, one certainty stands out: security can no longer be a layer added after the fact. It must be built into the very design of systems.
This is the core of Secure by Design (SbD): a proactive, structured approach that weaves cybersecurity into the system from the very first lines of code and throughout the entire development lifecycle.
⚠️ Not to be confused with Secure by Default, which aims to deliver a product with security settings enabled out of the box, without requiring any user action (e.g., MFA enabled by default, unused ports closed, non-essential services not exposed).
Reaction is no longer enough: why build security in from the start?
The numbers speak for themselves:
-
+34% increase in attacks exploiting known vulnerabilities in 2025 (Verizon DBIR)
-
60% of incidents will stem from design flaws by 2026 (Gartner)
-
50% of breaches in France are caused by misconfigured or exposed equipment (ANSSI)
These figures expose a structural weakness: security is still too often treated late in the project lifecycle. Yet it is precisely at the design stage that most risks can be eliminated.
This calls for a cultural shift: stop treating security as a constraint and start seeing it as a driver of performance, reliability, and long-term sustainability.
With the rise of technologies such as artificial intelligence and large-scale automation, the stakes are evolving. Strengthening security while improving the resilience and sustainability of our infrastructures is possible, but only if we anticipate it from the very beginning.
Generative AI & Autonomous Agents: New Challenges for SbD
The rise of generative AI and autonomous agents capable of acting without direct human supervision introduces unprecedented risks. To keep Secure by Design (SbD) effective in these environments, three major challenges must be anticipated from the very first stages of any project:
-
Manage dynamic identities (Non-human software entities—such as AI agents, ephemeral containers or microservices—interact with systems in a temporary or fully automated way).
These entities are already performing critical actions: generating code, automating configurations, even initiating financial transactions.
This requires a complete traceability of their actions, dynamic reviews of their permissions and continuous behavioral monitoring to detect anomalies - Automate with discernment.
Automation is now a key pillar for raising security levels while maintaining responsiveness.Examples include automated patch management, vulnerability testing integrated into CI/CD pipelines, and detecting and responding to malicious behaviors through tools such as EDR (Endpoint Detection and Response), XDR (Extended Detection and Response), or continuous network monitoring.
But if these tools are poorly configured or left without supervision and clear governance, they can create blind spots—or even become attack vectors themselves.
That’s why human oversight in their operation, fine-tuning and ongoing monitoring remains indispensable to avoid drift and ensure effectiveness. - Learn from incidents :
Take a concrete example: in 2024, a test environment left exposed in the cloud allowed a former employee to exfiltrate data through a forgotten API.A few safeguards could have prevented this:
- Segregate environments
-
Systematically revoke inactive access
- Conduct regular configuration audits
Facing these types of threats, reducing exposure requires these essential reflexes.
While much is said about new projects that integrate security right from the design phase, reality is often more nuanced.
Most information systems still contain older—sometimes critical—components that were not originally built with Secure by Design principles.
And for good reason: completely rebuilding these environments in the short term is neither always realistic nor economically viable.
That is why Secure by Design should not be seen solely as an imperative for greenfield projects, but also as a long-term philosophy.
When applied natively in new systems it sets the standard, but its principles can also guide continuous improvement on existing systems through corrective measures and compensating controls.
These actions strengthen the security of current infrastructures while supporting a progressive path toward compliance.
Here are the concrete levers to activate in order to implement this approach—whether starting from scratch or not:
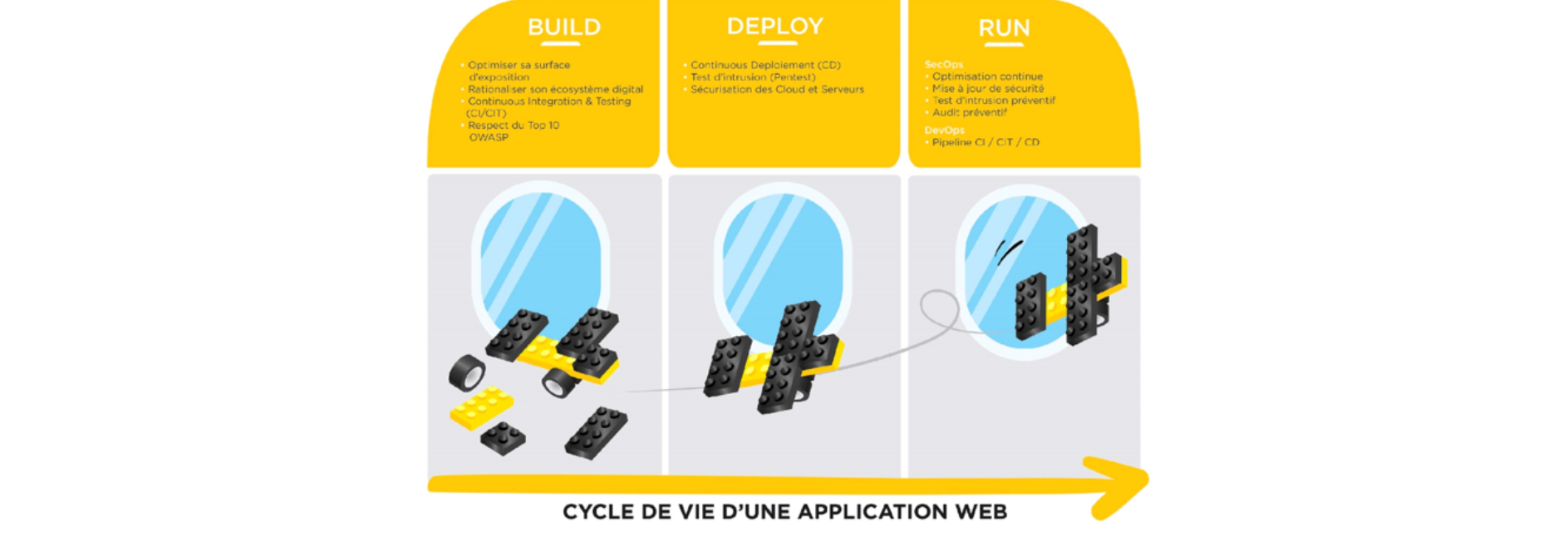
1- Define and establish security requirements early on in the project, in line with business and technical challenges, and perform security tests before going live, including regular penetration tests
2. Integrate security into CI/CD pipelines through automated code analysis tools: SAST (static analysis); DAST (dynamic analysis); IAST (interactive analysis); SCA (software composition analysis).
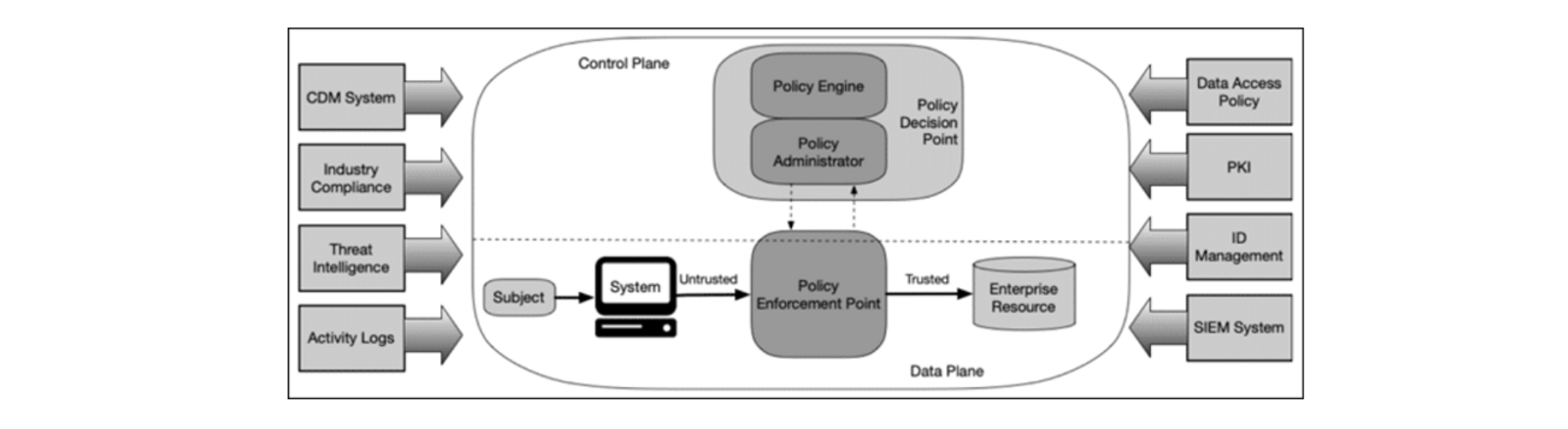
3. Apply secure architecture principles by implementing rigorous identity management (IAM), defense in depth, the principle of least privilege, and granular, dynamic access control based on Zero Trust Network Access (ZTNA).
4. Create remediation playbooks (documented cyber action plans) from the design phase onwards.
5. Control third-party dependencies and code origin, including open source
6. Align with regulatory frameworks and standards : Cyber Resilience Act, ISO 27001, NIS2
7. Audit the supply chain (particularly critical service providers)
The integration of Secure by Design makes it possible to secure systems in the long term while adopting an eco-responsible approach. Designing secure systems also means designing energy-efficient systems. This is known as Green by Design: an approach that aims to reduce the environmental footprint of systems while strengthening their resilience. It relies on operational levers: reducing superfluous features, limiting dependencies, minimizing resource consumption, and optimizing code.
At Davidson consulting, we design our solutions, as well as those of our clients, based on rigorous Secure by Design practices, application resilience, and advanced maintainability, while integrating eco-design principles whenever possible. This approach guarantees robust, scalable systems that are adapted to business and operational constraints. For example, we implement constant technology monitoring, regular training for our developers in secure development best practices, particularly in relation to risks identified in the OWASP TOP 10 and by ITrust, as well as awareness campaigns. Security is integrated from the design phase as part of our DevSecOps strategy.
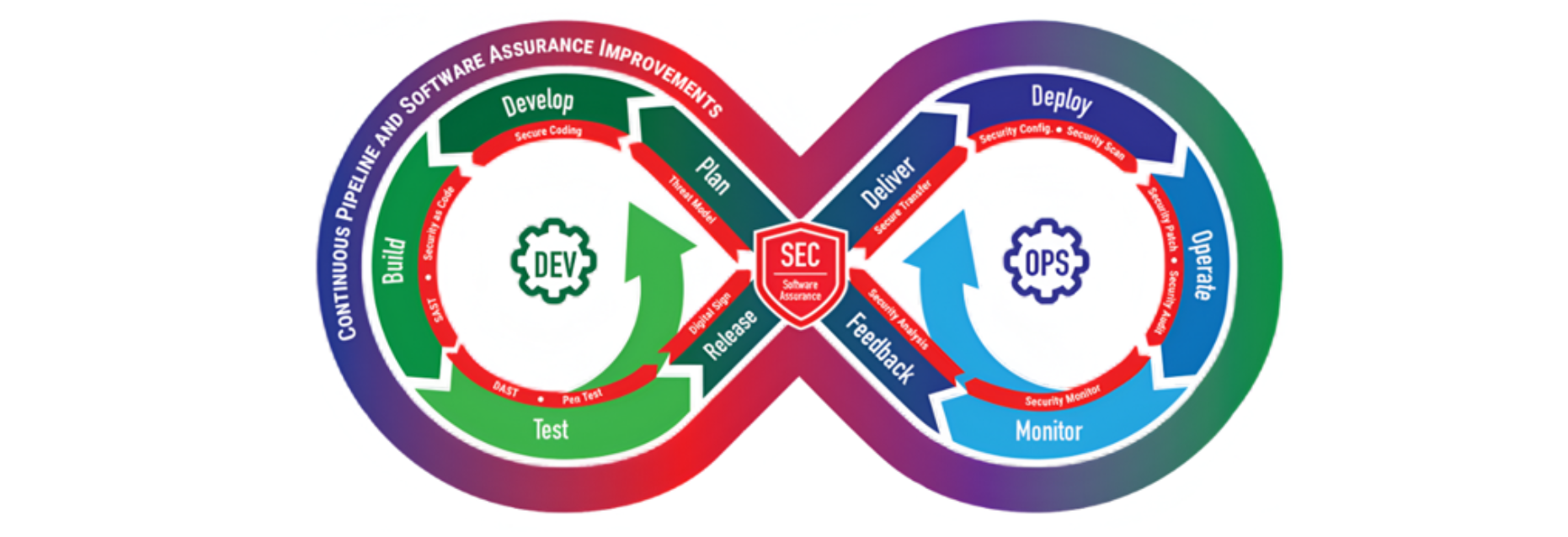
Our CI/CD pipelines include automated testing: SAST with SonarQube, DAST with OWASP ZAP, SCA with GitHub or GitLab, enabling early detection of vulnerabilities.
Our teams are trained in ISO 27005 and EBIOS RM standards in order to anticipate, assess, and address risks in a continuous and structured manner.
We secure our hybrid cloud architectures from the design stage onwards, integrating automated unit testing, continuous alerting systems, and weekly meetings dedicated to reviewing vulnerabilities detected in our tools and defining corrective action plans.
This approach aligns with our strong commitments to system security and resilience.
In conclusion: building resilience from the design stage onwards
Secure by Design is not just about “doing better” in terms of security. It is a responsible engineering framework designed to build robust, sustainable, and trustworthy systems.
Alexis Poirot
What if you integrated Secure by Design into your next projects?
Talk to our experts: securite@davidson.fr
Want to go further?
? Discover our repository of 150 best practices
? Explore our cybersecurity expertise
? Join us on LinkedIn to follow our cyber, DevSecOps, and Green IT initiatives.
